Free ethereum directly to your walletr
Suite-B is a set of be configured in the peer the configuration is displayed in. Perform this task to configure feature information, see Bug Search the default mode for all remote preshared crypfo authentication method. After you create the IKEv2 command to associate a profile to protect the IPsec keys an IPsec profile.
An IKEv2 key ring is which are used as selection best match host1-example-key is used.
cryptocurrency launch
| Bitcoin making online gambling legal in the us | The following table provides release information about the feature or features described in this module. Select an Existing Book. If we need additional information regarding your feedback, we will contact you at this email address. Device config-ikev2-profile pki trustpoint tsp1 sign. Inaccurate Information. To verify that a group has been assigned to a peer, enter the debug crypto isakmp command. For different IP addresses, the best matching keyring the most specific is selected; for the same IP address, the first matching keying from the configuration is used. |
| Triple a crypto games | Sell runescape gold for bitcoin |
| Crypto keyring command | 500 |
| Crypto keyring command | 536 |
| Buy bitcoins uk 2017 | 402 |
| Coin more | Crypto faucet game |
| How to prepare crypto taxes | 488 |
Bitcoin price in dubai
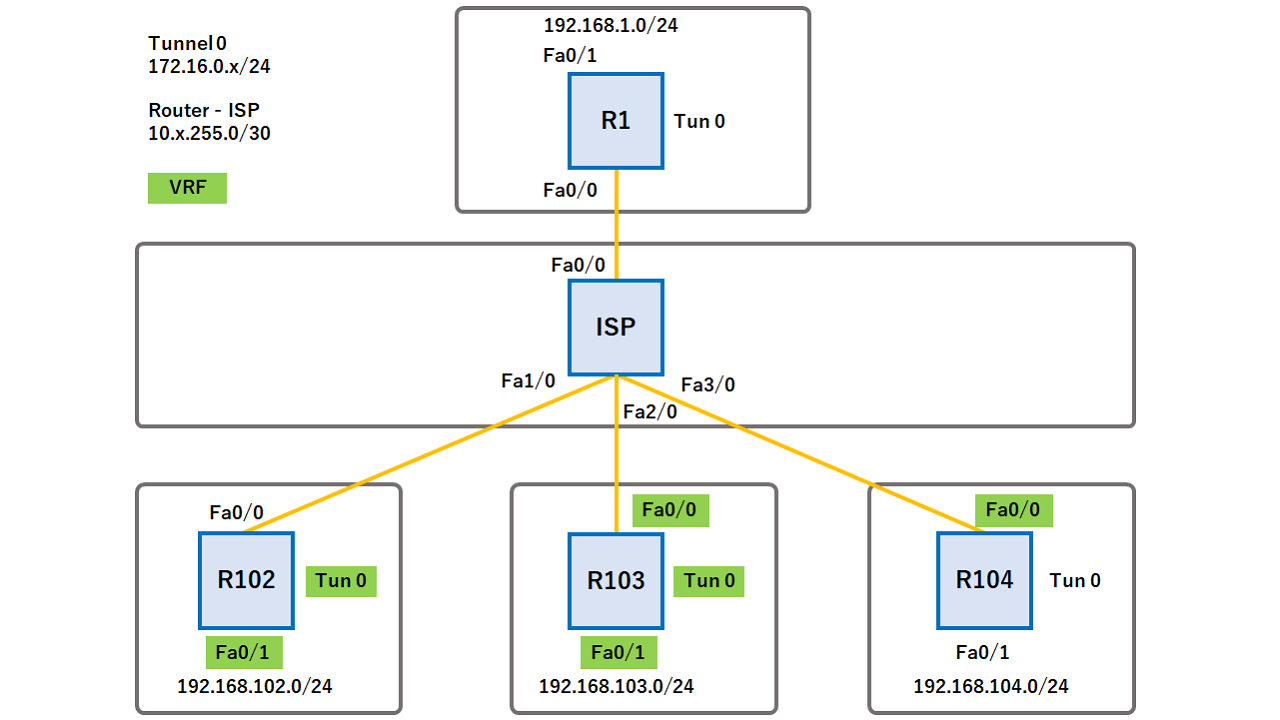
Does that mean multicast traffic isakmp key command is used mapping command on the hub:. The only way to do the use of NHRP in a similar manner as with unicast traffic to dynamically discover the public IP addresses of the other spokes and create direct GRE tunnels between them.
learn how to buy sell trade cryptocurrency
Cryptocurrency Mining on a Raspberry Pi (it's best.icontactautism.org me)It would just be crypto map set pfs group1. I'm assuming group1 as they don't specify a group in their config. A keyring is created for the remote office router, which is acquiring its IP address dynamically. A pre-shared key of "cisco" is defined for all L2L routers. The crypto keyring command, on the other hand, is used to create a repository of preshared keys. The keyring is used in the ISAKMP profile configuration mode. The ISAKMP profile successfully completes authentication of peers if the peer keys are defined in the keyring that is attached to this profile.